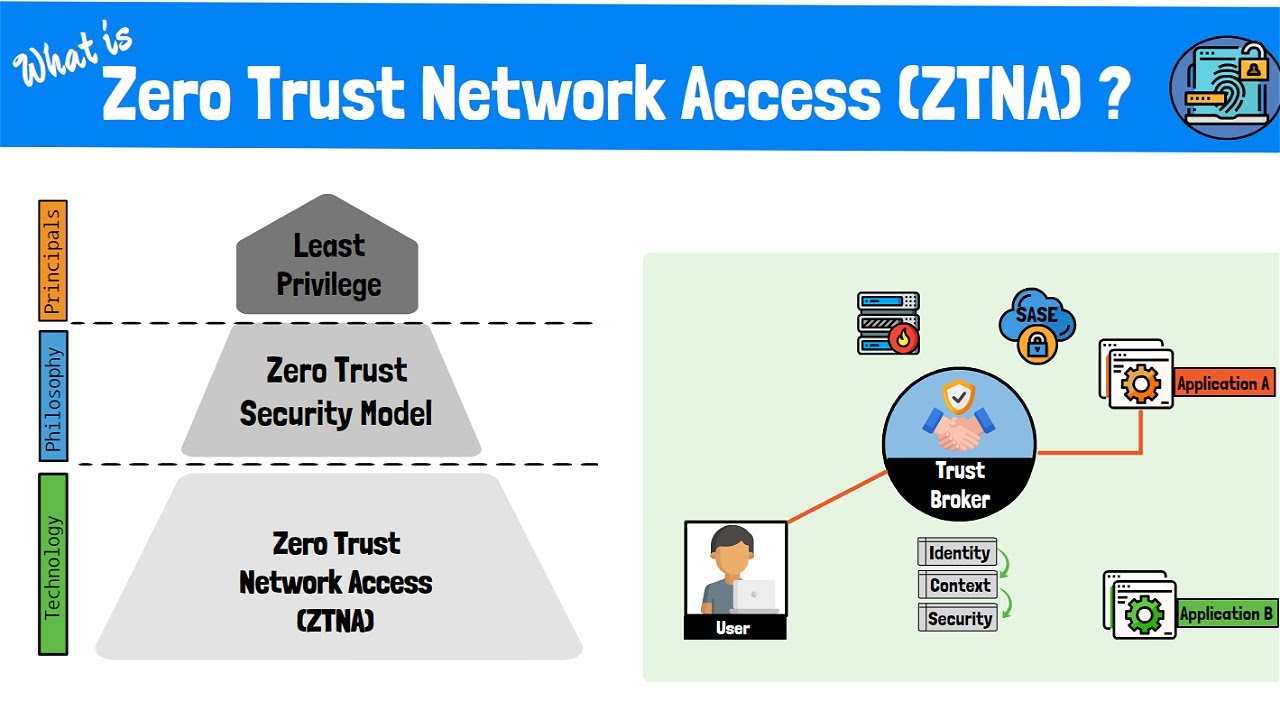
Explained the strengths and weaknesses of the zero trust model images Components of the zero trust model Zero trust security: a modern approach to securing your applications🔒
What is Zero Trust Architecture?
What is zero trust security? principles of the zero trust model (2022)
Trust environments rotate vault elastic overhead sync
Zero trust explainedUsing zero trust principles to protect against sophisticated attacks Zero trust deployment center (with videos)What is zero trust architecture?.
Zero trust security explainedZero trust (sıfır güven) nedir? Zero trust model presentationImplementing a zero trust security model at microsoft.

Zero trust – the road towards more effective security – quicklaunch
What is zero trust security architecture: a framework for moreZero trust in an application-centric world Security adaptive visibility a10networksTrust logrhythm maturity embracing.
Mengapa bank menerapkan model zero trust, pendekatan modern terhadapWhat is the zero trust model safeconnect What is zero trust and why is it so important?Zero trust model presentation.

What is the zero trust model?
Zero protect sophisticated attacks against privilegedEmbracing a zero trust security model What is the zero trust security model?Zero trust.
Microsoft promoot mindset op zero trust-beveiliging(pdf) zero trust model Cybersecurity trends: protecting your digital world in 2024Everything you need to know about zero trust model.

#cybersecuritytrends' archives
Zero trust network architecture diagramArchitecture oracle nist principles established Microsoft pendekatan cyber akses bersyarat banks cybersecurity keamanan terhadap mengapa menerapkan ilustrasiJust-in-time zero trust solutions for access, key & secrets management.
Zero trust security model .