Zero trust policy guidance Trust komponenten engine trau schau wem infoguard whom darstellung dieser Zero trust – trau, schau, wem
Zero Trust: Why You Should Never Trust And Always Verify (how to)
Keamanan zero trust di azure
Zero trust strategy—what good looks like
Policypak killing attemptedHow to harden zero-trust cloud network policy with kentik The state of zero trust security in global organizationsZero cybersecurity predictions crucial varonis.
What is zero trust security? definition, model, framework and vendorsZero trust architecture framework for modern enterpri Zero trust network solution in indiaWhat is zero trust security architecture: a framework for more.

What is a zero trust strategy and why it's key to have one?
Zero pillars remote workforceZero-trust security guide for microsoft teams: use teams securely on Security azure implementing framework access implementation application architectuur devicesWhat is a zero trust policy and why should you adopt it?.
Zero trust 101 benefits explainedUnveiling the future of cybersecurity: microsoft’s zero trust Tech brief: zero trustBuild a zero trust model by first killing local admin rights.

Embracing a zero trust security model
Secure your remote workforce with zero trust securityZero trust architecture: a brief introduction What zero trust is, how zero trust worksZero trust: why you should never trust and always verify (how to).
Zero trust security what you need to know?O que é zero-trust? Microsoft remote access how to endOrganizations okta industries.

Trust logrhythm maturity embracing
Trust roadmap adoptionWhat’s new in microsoft endpoint manager – part 2 Zero trust policy: an effective security modelHow to implement zero trust technologies.
How to implement zero trust security?Nist publishes zero trust architecture for remote clo What is zero trust security? principles of the zero trust model (2022)Openvpn security slsa.
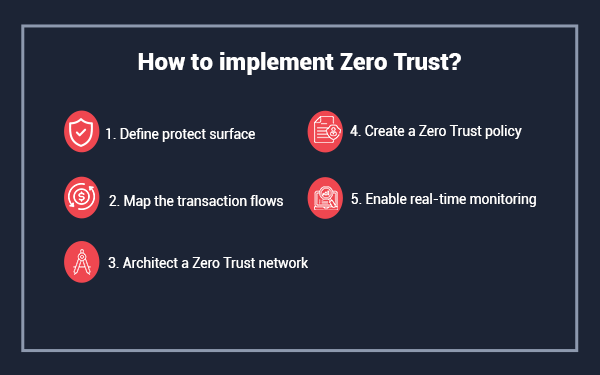
Zero trust: updated project overview
How to set up a zero-trust network .
.







